In early April, it was reported that there had been a Facebook data leak, raising alarms among Facebook account holders. Half a billion Facebook accounts were impacted. The dataset is from 2019, so it had been out there, but not widely circulated. Over the weekend, the data started popping up on popular hacking forums for free. The interesting story is where the data likely came from, what can be done with it, and what you can do to protect yourself.

What was in the April 2021 Facebook data leak?
Data for more than 500 million Facebook accounts was included in this data dump. It appears that most records included Facebook ID numbers, names, gender and phone numbers. Some records also included birth dates, location, relationship status and employer.
Most of this data does not seem to have been acquired through typical data breach methods, meaning it wasn’t collected by breaking into Facebook’s databases. Instead, it was “scraped” from information that users themselves made visible.
Attackers scraped Facebook data by exploiting a vulnerability in Facebook’s Contact Importer feature in 2019. From what has been reported, the individuals probably used Android emulators, which is software that simulates an Android device on a computer. They loaded, say, 10k phone numbers into the address book of the emulated device, installed Facebook’s mobile app, and used the app’s “import contacts” feature to get the rest of the profile data for those 10k phone numbers. Then they wiped the device and did the same thing with another batch of 10k phone numbers, etc. etc.
A combination of privacy settings led to data vulnerability:
- Profile data being set to “Public” or share with “Friends”
- In Facebook privacy settings, people had “who can look you up using the phone number you provided” set to “Everyone”
Recommended security steps
Even if your Facebook login, email or password information isn’t in this dataset, your phone number may still be vulnerable. You can check to see if your phone number was in the leak at haveibeenpwned.com.
If you have ever signed up for a Facebook account — even if you don’t use it now — we recommend you take these steps to protect yourself:
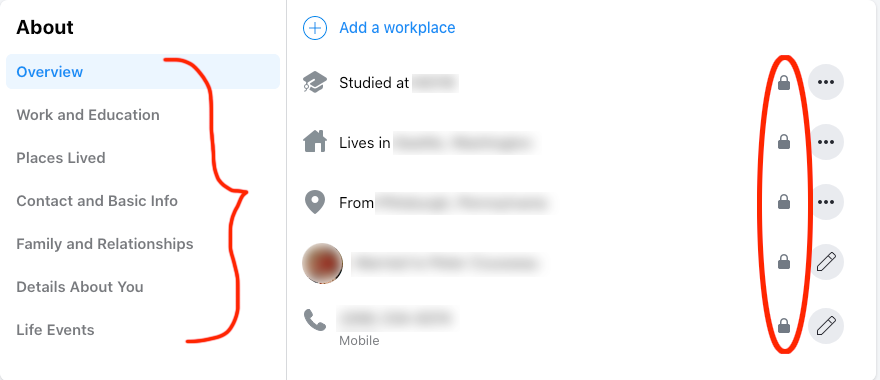
1. Change your profile information to private in your Facebook privacy settings.
During this breach, hackers took profile information that was set as open to “Public” or shared with “Friends.” This information can be matched and combined with data from other breaches to access even more of your personal information and accounts.
Visit https://www.facebook.com/me/about. Go through all of the sections in your Facebook profile on the left, and consider setting them to Private or Friends on the right. The less you make public, the more private and secure you will likely be.
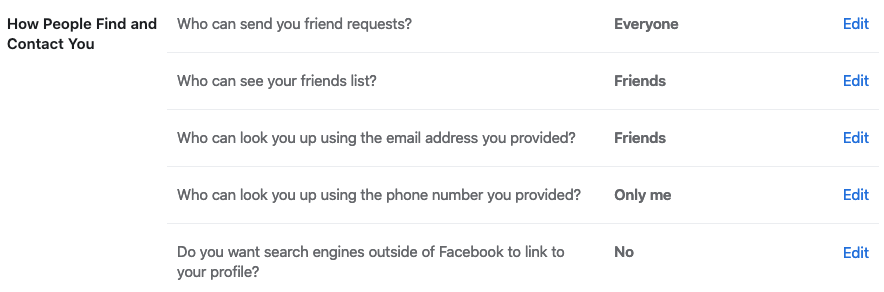
2. Adjust who can find and contact you on Facebook. Visit your Facebook Privacy settings and set them all to Friends or more strict for stronger security.
3. Change the passcode or PIN on your mobile phone carrier accounts to prevent SIM swapping. SIM swapping is when a criminal uses phone numbers, date of birth and other data to take over a person’s cell phone number and then hack into their email, social media and even financial accounts. Learn more about how SIM swapping works.
4. Review all of your Facebook privacy settings. As the Facebook platform evolves and grows, parts of your account could be public in surprising ways. Data could also be collected and shared in ways you don’t know about.
5. Sign up for Firefox Monitor to see if your email address has been part of a previous data breach and get alerted to future ones.
The bottom line is you don’t need to wait for a data breach to get smart about your security. Being alert to issues like data breaches and SIM swapping is part of modern internet citizenship as we do more with our devices and live online.



