When US General George Marshall saw Nazi propaganda films for the first time around 1940, he took away the three-time Oscar winner Frank Russell Capra and, in turn, ordered a series aimed at changing public opinion in the US in favor of a war effort. The extraordinarily successful series that Capra produced was called “why we fight” and popularized a propaganda term that remained essential to the world until 1990, the term “free world”.
For a short time in 1990, it seemed that the Free World had won. In reunified Germany, memories of the great demonstrations of the early 1980s faded against census, state surveillance and invasion of privacy. Especially the adolescent generation discovered the computer as a great way to escape parental supervision while watching TV next door.
In August 1981 IBM had presented its first PC and opened up together with upstarts such as Apple, Commodore or Atari a completely new market. The approximately simultaneous onset of video games (Pac Man was released in 1980) gradually led in Germany to the fact that the population discovered the computer as a social opportunity. The computer was no longer state-owned, but “personal”. He no longer appeared as a threat, but as a promise.
Even in East Germany in the late eighties, despite the economic embargo, there were an estimated 200,000 Commodore 64 or Atari ST, which were traded for the price of a new car between 12,000 and 40,000 marks. The “state-owned enterprise” Robotron had developed with the Z1013 an Eastern European PC, but he came, like everything one would like to have in East Germany, with a year waiting time and as a kit.
The question of the computer in society subsequently broke away from the civil rights movement. It now appeared in the context of innovation and economic policy and privacy was recuced to the mere right not to see advertising. In Germany Facebook and Google are launching large campaigns in the fall of 2018 that want to keep the problem within that framework, even though it’s all about scenarios far different than clicking an ad banner.


Who controls the German data?
In the same year as the reunification, the Internet was released for commercial use. The first search engine (Archie) appeared in 1990 and three years later followed the first advertisements on websites.
At that time, the Germans searched the Internet mainly with the machines from Altavista and Lycos Europe, which since 1997 belonged to the then largest media group in the world, the German Bertelsmann Group. Four years later, Google had pushed all competitors out of the market. Lycos was bankrupt and Google’s market share in Internet search has since been over 90 percent. If you want to talk about German data, you have to talk about Google.
The great achievement of Google was to connect the science-state part of the Internet with the commercial one. Larry Page and Sergey Brin, who were initially committed to university principles, realized that a search engine needed to be dynamic and intelligent in order to deliver relevant results. Eric Schmidt, who joined Google in 2001, commercialized the search engine.
Both only worked with a tremendous amount of data. Programming an algorithm that combines a user’s search query with other data to guess what the user is really looking for is in itself not puzzling. But if the algorithm is to be the best in the world, the machine has to find ever finer types and categories, and it needs to be used as frequently as possible.
On top of that, when advertising was new on the Internet, the advertising industry wanted to understand how many users clicked on their advertising banners, and they found it just as interesting what users do when they’re not clicking on the banners. Google had a brilliant solution for both questions.
The tracking software from Urchin was able to evaluate user behavior on a website within 15 minutes at the end of the 1990s. Before Urchin, this process took 24 hours, so it was not surprising that Urchin became the standard analysis tool within a few months.
In 2005, Google bought the company, named the service Google Analytics, and provided the software, like all its services, free of charge (not to be confused with free). Google was now able to conclude bets with its customers on which pixel a user clicks with what probability and negotiate the price via Google Adsense.
Obviously, the data that Google collected to prove the effectiveness of the advertising also works as metadata. For the history of metadata, it is critical that the chain of information always ends up with a single person, because the ultimate goal is to provide custom advertising to users.

This is why metadata is always tied to an individual, although in many cases it is quite sufficient for the innovative process of product development to collect anonymised data. If companies want to know who they are dealing with, there are basically two motives: either you want to sell someone or you want to monitor them.
The infamous quote from Eric Schmidt – “We know where you are, we know where you were, we know more or less what you are thinking about.” – is the result of a humanistic interpretation of economic data. But it is also the foundation of one of the most successful business models in human history.
Google was the first company to recognize that the interpretation of data is the contemporary version of mind reading, and from the human understanding that results, Google has developed products that people really wanted.
The amount of data needed today to compete with a machine like Google can only be produced in English and Chinese. It may be possible to be better in niches and at the local level than Google (in Germany, search results are often weak at the local level), but on more general issues the market will no longer be able to produce an alternative on its own.
The situation is different with social networks. They can basically be easily replaced by others, as the example of Myspace and StudiVZ impressively demonstrate. It says a lot about the German users at the beginning of the years 2005-2007 that they have also decided here against a German and for an American variant.
Why did German social networks not succeed?
At the end of 2006, Marc Zuckerberg called the two German founders Ehssan Dariani and Dennis Bemmann and offered them six percent of Facebook shares (today’s value over $ 20 billion). Dariani and Bemmann had something that Zuckerberg did not have: a social network in Germany.
StudiVZ, that was the name of the network, had nearly 20 million users and although the network was a cheeky copy of Facebook, it seemed impossible then to displace StudiVZ from the German market as a US American network. However, the network had a catch: If you wanted to spy on a passing university acquaintance a little, this got the visitor in a message window.
“No one was willing to give this nakedness,” wrote a user in farewell to StudiVZ. In 2006, Facebook could anonymously scroll through the Friends of Friends’ profiles, without them noticing something of the visit. Although Facebook 2007, a year before its German-language version, with a Web Beacon already triggered its second privacy-related scandal, surpassed the number of users the network its German competitors in 2009.
Facebook became the largest social network in the world, even though it was already clear at that time that the privacy policy was much looser for US companies than for German companies.
In the meantime, StudiVZ had been sold to the publishing house Holtzbrinck and the strategy of the publisher was: we will not do anything that contradicts German data protection. Holtzbrinck managers later claimed that Facebook’s second attempt to buy the network failed because of the stringent German privacy policy.
The Facebook negotiators immediately recognized that the strict German data protection did not fit their business model and it was much better to use the regulatory gaps of the Internet to register German customers under the conditions of loose US privacy policy.
In retrospect, the years 2006/2007 therefore appear as a decisive turning point, because in the same year Google took over the already very popular video service YouTube in Germany and started the map service Google Maps. Germany finally lost control of the Internet and had to trust that private companies in the US would be responsible for the privacy of the German population.
The increasing data flow from Germany to the USA interested not only private advertising companies, but also the intelligence services and the surveillance industry. It played a major role that Germany – since 1945 one of the most competitive espionage areas in the world – after September 11, 2001 was under general suspicion.
Does Facebook owe its success to terrorism?
A few days after the attack on the World Trade Center on September 11, 2001, it was clear that the assassination attempt had been planned in Hamburg. “We are a small group of young men from different Arab countries,” Mohammed Atta wrote by email several months before the attacks and “would like to start training for professional aircraft pilots.”
US security services knew the men wanted to enter, and there were many suspicious moments waiting to be combined in CIA computers. But just like the murder of German employer President Hans-Martin Schleyer in 1977, a possible prevention failed because human error did not produce the right metadata.
John O’Neill, head of FBI counterintelligence and a kind of Captain Ahab anti-terrorist supporter, warned of a 9/11 attack on Al Qaeda in the US. He has persecuted Osama Bin Laden for years and was one of the most prominent experts in the terrorist network.
Had the CIA informed O’Neill that two of Bin Laden’s closest associates were about to enter the United States with visas, he would probably have switched immediately. Instead, he quit the service in frustration and died under the rubble of the World Trade Center, where he had begun serving as security chief a few days before the 9/11 attack.
The US responded to this glitch with the government program “Total Information Awareness”. The official name was later renamed “Terrorism Information Awareness” for a good reason, but considering what happened on the Internet afterwards, the first name was the much more apt name.
The initiators of the program wanted to keep people out of the process as the weakest link in the chain and to transfer the investigative work to supposedly incorruptible algorithms. The method underlying the TIA was therefore nothing more than a globalized, negative dragnet, which had been invented in Germany in the 1970s by BKA boss Horst Herold (see part 1)
The security architecture received completely new foundations and mass data collections were the result. Security authorities were given far-reaching rights over “suspects” and, in case of doubt, could themselves decide who or what was meant by the term “suspect”.
But at the beginning of the millennium, it was not so easy to collect the right metadata and combine it. German investigators evaluated 8.3 million records after the attacks, but were only able to initiate a single investigation. No wonder, then, that the security services cast a jealous look at the commercial data of emerging Internet companies.
It was difficult to argue against the crass invasion of privacy immediately after 9/11. Even civil rights activists and activists were in shock and accepted the situation as an exception. However, the German Bundestag extended the actually limited to five years law for another five years and gave the law the sonorous name “Counter Terrorism Supplementary Act“.
The net had finally lost its innocence. The query of banking, airline, postal and telecommunications data was now easier and the online search of private computers soon became part of the standard program of the police. The security authorities kept data in reserve and consolidated their databases into an Internet-based Internet.
All this would have had little success, if not a huge data industry had emerged at the same time, which pulled the people out of their pockets when shopping the personal desires and preferences and recorded private conversations, movement profiles and even the mood after getting up and evaluated.
Governments would have acted against their own interests if they had tightened up a group like Facebook or prevented them from collecting data, because the state would never have been able to procure that vast amount of personal information in any other way.
If we can outwit death, do we have to accept crime?
The Internet is a cable medium, which becomes immediately noticeable when you connect a computer directly to the cable network via a LAN connection (the share of data transfer via satellite is still in the small single-digit percentage range) and these cables belong to someone.
Nearly four billion people use the Internet. But there are only just over 400 submarine cables that hold the Internet together. Apart from the most modern and fastest cable that Facebook and Microsoft have laid from Virginia Beach to Bilbao, the deep-sea cables are large consortia that do not compete with each other, but each organize a world region. America is supplied by TE Subcom, Asia by NEC. The European network belongs since 2016 to the Finnish Nokia.
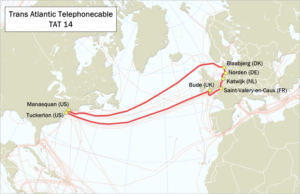
For secret services, these are paradisiacal conditions. To Germany, the data come predominantly on the Transatlantic Telefonkabel No. 14 and it is probably impossible that the British secret service GCHQ and the NSA record almost all telephone calls from Germany, without having agreed in any way with the network operators.
The ability to generate more and more metadata has fundamentally changed policing. The “criminal geology” that Horst Herold invented in the 1970s wanted to calculate when and where with what probability a crime would be committed. with today’s metadata you move on to a decisive (and highly debatable) step. One wants to predict who will commit the crime.
As late as August of 2018, Joachim Eschemann, head of the department for crime affairs in the Dusseldorf Ministry of the Interior, said that you really do not need any personal data if you want to prevent crime in a particular region. The identity of the offender plays a role in the investigation after the fact.
The police in Hessen nevertheless believe that what needs to be done is what needs to be done. To the horror of civil rights activists, she uses software from the company Palentir, which was co-founded by the German investor legend Peter Thiel and which bears the name of a city from the Batman saga: Gotham.
Gotham is there to predict crimes, so the software combines existing information from police databases with openly visible information from social networks. Peter Thiel, who as a supporter of transhumanism does not even accept death as an immutable fact, can not, of course, stretch his arms over something as earthly as crime.
But Thiel is not the only one who stands for a strange turn of the Silicon Valley to the state. There seems to be an unwritten law after immeasurable wealth inevitably leads to politics. Just having money is boring and since you’ve always wanted to change the world, it makes sense to switch sides.
Eric Schmidt, who advised Obama and later Hillary Clinton in 2009, moved to the Pentagon after leaving Google 2016. He is presumably genuinely convinced that the world of attacks and assassinations we’ve been living in since September 11 can only be freed by a meta-algorithm.
The only way, according to Schmidt 2010, to counter threats in the network is real transparency and not anonymity. “In a world of asynchronous threats, it’s too dangerous to forgo a way to identify people. We need a name service for people. Governments will demand that.”
How could it possibly come this far?
The Internet not only gave birth to a technological apparatus, but a new dimension that legally did not belong to the land, to the sea, nor to the air, and therefore was hardly judicable with conventional terms. It gave the impression that the Internet was a lawless space. The terminology of the “old world”, which described the classic media radio, newspaper and television, did not fit on the Internet.
In the 16th century, after the discovery of the New World, the British Empire had responded to a similar situation with a breathtaking trick. Knowing that British courts could not speak right across the world, the Empire introduced the so-called “amity lines” – a pragmatic line on the world map that divided the world into two spheres: one in which European treaties were valid, in the other was the right of adventurers and conquerors. The twentieth century did the same. It devided the world in online and offline.
The English, in the sixteenth century, had drawn yet another “amity line,” which was more a narrative than a real separation; which, however, is at least as important for the Internet and for privacy in Germany as the distinction between online and offline. It reads: What belongs to the field of the economy, is private and does not belong to the sphere of the state.
The political separation of the world into online and offline and the simultaneous liberal-neutral attitude towards companies that shared the Internet, led to the living situation in which the individual has little to expect from the state. With bitter irony one could say: On the Internet, the protection of privacy is a private matter.
A not insignificant role was played by a short, but violent political movement, which always wants the good and always creates the evil, because they saw in the existence of the Internet has a value to itself and seriously demanded that society now had to adapt to the Internet, although one could think at least in Germany, it would be more meaningful the other way round.

Among the geeks of this movement, who pretended that the Internet had been invented only around the year 2000 and as if it had nothing to do with the state, there was a group of activists who were quickly feared by politicians as so-called “net community”.
The term “shit-storm” did not happen to find its way around the year 2006 in the German language, which uses the term – unlike English – only for a hateful, undifferentiated discussion on the Internet. In 2011, a jury voted the term Anglicism of the Year in Germany.
A shit-storm, in particular, covered those politicians who dared to regulate “the Internet” and because the established parties feared that the Pirate Party would disrupt the party landscape in much the same way as the Greens did in the early 1980s. they thus kept their fingers off the Internet. The Free Democrats campaigned in the general election campaign 2018 with the slogan “Digital first. Concern second. ”
As a result, in the crucial years between 2005 and 2010, no one seriously developed an interest in preventing Internet companies from collecting and storing personal information. On the contrary, it is precisely the state authorities that have made the current situation possible through a combination of ignorance, incompetence and intelligence interests.
What now?
The ability to persecute individuals inevitably leads to a sense of being under surveillance, and even those who think they have nothing to hide will behave differently when they assume that everything they say is heard and evaluated.
The IT industry needs data to develop new products. But it is dependent both economically and socially on a functioning privacy. A democracy without data is conceivable, innovation without privacy in the long run is not.
We all probably want to use services like Google Maps and these products do not work without personal data like motion profiles, start and end points of a journey. The programmers of these services need to know that a person is going from point A to point B and how fast he is going to get on. The question is, of course, whether the service needs to know who that person is.
Of course, there is also a legitimate interest in integrity and security. That’s why there are now more than 200,000 public security cameras in London, which will deliver crisp images with the new G 5 standard. The question is whether the price of total surveillance of a population suspected of being a general suspect is an appropriate price for gaining security.
What do we think of Stanford University people using public funds to work on software that can tell if a person is homosexual? Does it concern us that in China, one of the most influential influencers for children is a chatbot from Microsoft (Xiaoice), who discusses dreams and fears with their underage interlocutors and stores and processes them?
Is it correct that Switzerland would like to systematically monitor its welfare recipients with GPS transmitters and drones, so that the rest of the Swiss society, from whose taxes social assistance is paid, can be sure that their fine money will not be embezzled?
It is the citizens who, at least in the Western world, can dictate that governments disclose what data our intelligence agencies collect and what happens with it.
The day after tomorrow there will be cars that generate 8 terabytes of data per day. Do we want that? Do we need to get back on the road to save the Internet for the next generation as a global and public resource that is open and freely accessible to all and leaves no one behind just because it wants to protect its privacy? If that does not work in Germany, there is nowhere. But if it works, it may work everywhere.
The End
READ THE SERIES:
<< Part 1: “You have to force them to leave tracks” || Part 2: “If we knew that, comrades, we wouldn’t be doing all this.”
This post is also available in: Deutsch (German)