Today we are announcing the relaunch of our web security bug bounty program, creating greater transparency into how we handle web security bug bounty payouts.
History
Bug bounty programs started a number of years ago with Netscape leading the way. In August of 2004, Mozilla joined in by launching our first bug bounty program. Funded by Linspire, Inc. and Mark Shuttleworth, it paid out $500 for critical security vulnerabilities found in Firefox and other Mozilla software. Although this may seem quaint in comparison to modern day bug bounties that can reach well into the six figures, at the time it was considered a revolutionary advance in how technology companies deal with the discovery of security flaws.
Six years later, in December of 2010, Mozilla was one of the first companies to add bugs found in their web properties to their bounty programs. Ranging from $500 up to $3000, it was another leap forward, this time focused on improving the state of web security.
From our first awarded web bounty bug (a cross-site scripting vulnerability in addons.mozilla.org) to now, we have paid out hundreds of thousands of dollars to researchers around the world who have lent their expertise to help us protect our users.
Challenges and Solutions
Bug bounty programs are always challenging to administer, especially for a company like Mozilla. We have staff and contributors that have lived and breathed the web for almost 20 years and our portfolio of websites has grown exponentially. From www.mozilla.org, to www.bugzilla.org to arewefastyet.com some of these sites create significantly more risk to Mozilla’s operations than others.
Problems have arisen with communicating this risk spectrum to bounty hunters. A hypothetical SQL injection on Bugzilla presents a different level of risk to Mozilla than a cross-site scripting attack on the Observatory or an open redirect on a community blog. To a bounty hunter, the level of risk is often irrelevant — they simply want to know if a class of bug on a specific site will pay out a bounty and how much it will pay out.
Overall, we think we have done a reasonable job listing the Mozilla websites that pay out bounties, but the actual payout amounts have varied. In addition, payouts have become more complicated for bugs discovered on sites that are not explicitly part of the program.
If a payout comes in at a level that meets or exceeds what the researcher was expecting, then everything is great. But if it comes in lower than expectations, a bounty hunter may be disappointed. Furthermore, making a payout exception for a given site creates an expectation that additional exceptions will be made.
Today
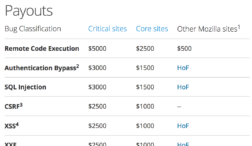
We are excited to relaunch our web based bounty program in a way that will address many of these historical issues while also expanding the number of websites and bug classes that are covered. In addition, we are explicitly listing how much each bug class will pay out and for what websites, based on their risk profile.
Having a clear and straightforward table of payouts allows bounty hunters to devote their time and effort to discovering bugs that they know will receive a payout. The hunters will also know the exact amount of the payouts. We’re also expanding the classes of bugs that qualify for our bug bounty Hall of Fame. Although these bugs don’t come with a monetary payout, it’s our way of publicly acknowledging the work of bounty hunters in making the web a safer place.
From our logos to our products, Mozilla is a company that prides itself on its openness. Although being open about payouts is generally unexplored territory, we hope that it helps contribute to greater openness in bug bounty programs around the web.
If you are an existing contributor to our web bug bounty program, we hope this structure helps focus your efforts. If you are just starting out, we look forward to working with you to help make the internet more secure!