This Valentine’s Day, Mozilla is assessing the privacy and security features of romantic connected devices
This Valentine’s Day, use protection.
To be more specific: use encryption and strong passwords.
As the Internet of Things expands, the most intimate devices are coming online. Sex toys and beds now connect to the internet. These devices collect, store, and often share our personal data.
Connected devices in the bedroom can amp up romance. But they also have the possibility to expose the most intimate parts of our lives. Consumers have the right know if their latest device has privacy and security features that meet their standards.
So today, Mozilla is releasing a Valentine’s Day supplement to *Privacy Not Included, our annual holiday shopping guide.

Last November, we assessed the privacy and security features of 70 popular products, from Nintendo Switch and Google Home to drones and smart coffee makers. The idea: help consumers shop for gifts by highlighting a product’s privacy features, rather than just price and performance.
Now, we’re assessing 18 more products, just in time for February 14.
We researched vibrators; smart beds and sleep trackers; connected aromatherapy machines; and more.
Our research is guided by Mozilla’s Minimum Security Standards, five basic guidelines we believe all connected devices should adhere to. Mozilla developed these standards alongside our friends at Consumers International and the Internet Society. Our Minimum Security Standards include encrypted communications; automatic security updates; strong, unique passwords; vulnerability management; and an accessible privacy policy.
Of the 18 products we reviewed for this guide, nine met our standards. Among these nine: a smart vibrator that uses encryption and features automatic security updates. A Kegel exerciser that doesn’t share user data with unexpected third parties. And a fitness tracker that allows users to easily delete stored data.
Nine products did not meet our Minimum Security Standards, or weren’t clear enough in their privacy policies or our correspondences for Mozilla to make a determination. Among these nine: a smart vibrator that can be hacked by spoofing requests. And a smart vibrator with no privacy policy at all.
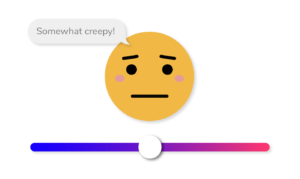
Lastly: This installment once again features the Creep-O-Meter, an emoji-based tool that lets readers share how creepy (or not creepy) they believe a product’s approach to privacy and security is.
Thanks for reading. And Happy Valentine’s Day
Jen Caltrider is Mozilla’s Content Strategy Lead and a co-creator of the guide.