The data URL scheme provides a mechanism which allows web developers to inline small files directly in an HTML (or also CSS) document. The main benefit of data URLs is that they speed up page load time because the inlining of otherwise external resources reduces the number of HTTP requests a browser has to perform to load data.
Unfortunately, criminals also utilize data URLs to craft attack pages in an attempt to gather usernames, passwords and other confidential information from innocent users. Data URLs are particularly attractive to attackers because they allow them to mount attacks without requiring them to actually host a full website. Instead, scammers embed the entire attack code within the data URL, which previously inherited the security context of the embedding element. In turn, this inheritance model opened the door for Cross-Site-Scripting (XSS) attacks.
Rather than inheriting the origin of the settings object responsible for the navigation, data URLs will be treated as unique origins for Firefox 57. In other words, data URLs loaded inside an iframe are not same-origin with their parent document anymore.
Let’s consider the following example:
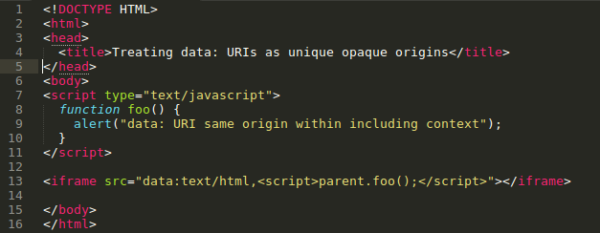 In Firefox version 56 and older, the script within the data URL iframe on line 13 was able to access objects from the embedding context because data URLs inherited the security context and hence were considered to be same-origin. In the specific example, the script within the data URL iframe was able to call the function foo() on line 8 which was defined by the including context and hence should be treated as a different security context.
In Firefox version 56 and older, the script within the data URL iframe on line 13 was able to access objects from the embedding context because data URLs inherited the security context and hence were considered to be same-origin. In the specific example, the script within the data URL iframe was able to call the function foo() on line 8 which was defined by the including context and hence should be treated as a different security context.
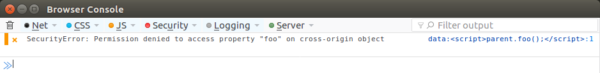
Starting with Firefox 57, data URLs loaded inside an iframe will be considered cross-origin. Not only will that behavior mitigate the risk of XSS, it will also make Firefox standards compliant and consistent with the behavior of other browsers. In Firefox 57, an attempt to reach content from a different origin (like the one from line 13) will be blocked and the following message will be logged to the console:
 Note that data URLs that do not end up creating a scripting environment, such as those found in img elements, will still be considered same-origin.
Note that data URLs that do not end up creating a scripting environment, such as those found in img elements, will still be considered same-origin.
For the Mozilla Security Team:
Christoph Kerschbaumer, Ethan Tseng, Henry Chang & Yoshi Huang