End users rely on the address bar of a web browser to identify what web page they are on. However, most end users are not aware of the concept of a data URL which can contain a legitimate address string making the end user believe they are browsing a particular web page. In reality, attacker provided data URLs can show disguised content tricking end users into providing their credentials. The fact that the majority of end users are not aware that data URLs can encode untrusted content makes them popular amongst scammers for spoofing and particularly for phishing attacks.
To mitigate the risk that Firefox users are tricked into phishing attacks by malicious actors encoding legitimate address strings in a data URL, Firefox 59 will prevent web pages from navigating the top-level window to a data URL and hence will prevent stealing an end user’s credentials. At the same time, Firefox will allow navigations to data URLs that truly result because of any end user action.
In more detail, the following cases will be blocked:
- Web page navigating to a new top-level data URL document using:
- window.open(“data:…”);
- window.location = “data:…”
- clicking <a href=”data:…”> (including ctrl+click, ‘open-link-in-*’, etc).
- Web page redirecting to a new top-level data URL document using:
- 302 redirects to “data:…”
- meta refresh to “data:…”
- External applications (e.g., ThunderBird) opening a data URL in the browser
Whereas the following cases will be allowed:
- User explicitly entering/pasting “data:…” into the address bar
- Opening all plain text data files
- Opening “data:image/*” in top-level window, unless it’s “data:image/svg+xml”
- Opening “data:application/pdf” and “data:application/json”
- Downloading a data: URL, e.g. ‘save-link-as’ of “data:…”
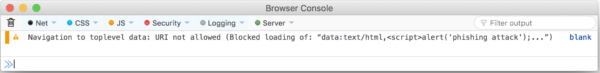
Starting with Firefox 59, web pages attempting to navigate the top-level window to a data URL will be blocked and the following message will be logged to the console:
For the Mozilla Security Team:
Christoph Kerschbaumer