The Mixed Content Blocker we described last month is now available in Firefox Beta and is on track for a general release in August with Firefox 23. When secure HTTPS pages load additional content insecurely over HTTP (a.k.a. Mixed Content), users are vulnerable to man-in-the-middle and eavesdropping attacks. The Mixed Content Blocker will block insecure active content by default, protecting our users from these attacks.
Call to Users – Report problems
If you find a website that isn’t functioning correctly because it contains insecure content that is being blocked by the Mixed Content Blocker, please let us know by sending an email to security@mozilla.org or commenting in our compatibility tracking bug
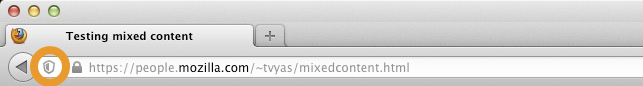
How can you tell if a site has Mixed Content that Firefox has blocked? Look for this Shield Icon in the location bar.
If you’d like to contribute further and help us find compatibility issues you can participate in our QA test day on Monday, July 1st.
Call to Web Developers – Test your site with Firefox Beta
If you rely on HTTP resources in your HTTPS pages this feature might break your website. If you do find Mixed Content issues on your webpage in Firefox 23+, chances are that the same issues exist in Chrome and/or Internet Explorer, who have also implemented this feature.
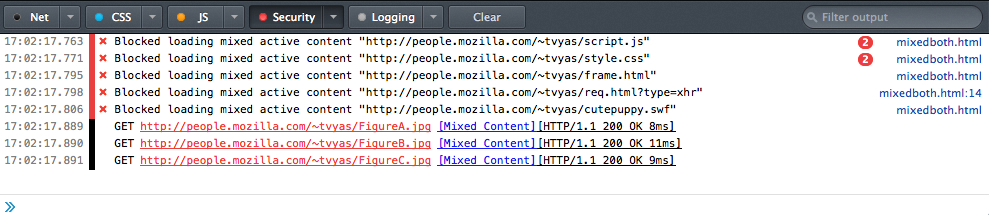
The best way to tell if your site will load correctly in Firefox 23 is to download the latest Firefox Beta and browse through your website with the Web Console open. Enable the “Security” messages in Web Console and check for messages about Mixed Content.
If you want to test your site in a more automated fashion, you can try using Skipfish, a web application security tool. Skipfish has a -M option that will report mixed content issues on your webpage.
To fix your site, simply replace http:// links with their https:// equivalents on your SSL pages. You can also use protocol-relative links if you use the same source code to serve your HTTP and HTTPS website.
If the Mixed Content resources on your page come from a third party, there is a chance that the HTTPS equivalent version already exists. For example, youtube.com has both HTTP and HTTPS video embed options. If the HTTPS version does not exist, consider contacting the third party (especially if they are one of your partners) and ask them to provide an HTTPS version of the content.
Call to Contributors – Contact Sites
We’ve been working on site compatibility issues, trying to find websites that are affected by the Mixed Content Blocker and alert them before Firefox 23 is released in August. However, finding accurate contact information for the affected sites has been a difficult task. And we could really use some help 😉
If you would like to contribute, please take a look at the list of affected sites and see if you can contact their website administrators and inform them of the Mixed Content compatibility issues that they are about to run into with Firefox 23 (and likely already have with Chrome or Internet Explorer). If you are able to find contact information and/or alert the website please let us know in the associated bug.
You can also help find more affected sites by participating in our QA test day on Monday, July 1st.
Want to Learn More?
Check out a more detailed blog post on this feature here.
XBOZ wrote on
wrote on
Daniel Veditz wrote on
wrote on
Michael wrote on
wrote on
Daniel Veditz wrote on
wrote on